Back to:
Top Teams
InsidePro Team
Resources
| Active Members
| 17+
|
| Handles
| .Scorpio., -=Cerberus=-, Admin, blazer, dda, gscp, h0wler, Kaiser, Lindros,
mastercracker, Mastermind, myslowtech, Polimo, proinside, test0815, Tyra,
usasoft, User
|
| Software
| EGB, Ppro, Hashcat suite, John the Ripper, others (see table below)
|
| Hardware
| 206+ various CPU cores, 42+ various GPUs (see table below)
|
Introduction
We cannot commend Korelogic enough for the effort they put in to
organizing `Crack me if you can' (CMIYC) at Defcon 21 this year. The
preparedness and organization of Korelogic simply put, was impeccable.
Big thanks go out to `Kaiser', our team representative at DC21 who had
the code to us before the competition was underway.
No words can describe how thankful we are to the software developers;
Admin from InsidePro, Jens Steube (Atom) and his hashcat-suite, the
entire JtR community, their work on John the ripper, and Gat3way for his
HashKill to name a few. The awesome work from these developers has truly
enabled us to push the boundaries of password cracking.
We would also like to congratulate our rivals Hashcat in placing second
and John-users placing a respectable third. It was also nice to see
other teams giving all their best. Shout outs goes to Teams; `Ralph
Wiggums Allstars', `Athena' and `Blow Cane' and also to the
teams/players part of the `Street' division. We would also like to
congratulate brad of '16 systems' in taking out first place in the
street division.
The Team
This year our team had 20 registered members however, due to busy
schedules we had 17 active members who were able to participate. Once
again, we had some new additions to our team which was comprised of:
.Scorpio., - =Cerberus=-, Admin, blazer, dda, gscp, h0wler, Kaiser,
Lindros, mastercracker, Mastermind, myslowtech, Polimo, proinside,
test0815, Tyra, usasoft and User. Due to our wide geographic
distribution across time-zones, we were able to consistently remain
active through the 48 hour period.
In anticipation for Crack Me If You Can (CMIYC) at Defcon 21, we had a
revised Hash management suite (HMS) prepared dubbed TeamLogic, which
was backed by our communication forum. Our HMS was a web based
application which automated the entire process of tracking all the
cracked/uncracked hashes and passwords as well as statistics for
algorithms and members. The forum was used for general communication
and delegation of distributed tasks.
The Gear
Hardware
| System Type | Count | Cores | NV GPUs | Count | AMD GPUs | Count
|
| Dual Cores | 4 | 8 | GTS250 | 1 | HD5750 | 2
|
| Quad Cores | 18 | 72 | GTX460 | 2 | HD5770 | 3
|
| Hexa Cores | 3 | 18 | GTX470 | 2 | HD5850 | 2
|
| Octa Cores | 2 | 16 | GTX560Ti | 2 | HD5870 | 3
|
| | | | GTX590 | 1 | HD6950 | 2
|
| High Performance | | | GTX650Ti | 1 | HD6970 | 2
|
| E5-405 x2 (cluster) | 4 | 32 | GTX680 | 1 | HD6990 | 1
|
| E5-430 x2 | 2 | 16 | | | HD7870 | 1
|
| E5-2650 x2 | 1 | 16 | | | HD7970 | 15
|
| E5-645 | 1 | 12 | | | |
|
| | | | | | |
|
| EC2 (cc2.8xlarge) | 28 hours | 16 | | | |
|
| | | | | | |
|
| Total | | 206+ | | | | 42+
|
We brought into the competition quite a number of high-end GPUs and
high-performance CPUs this year, doubling the number of HD7970s and
more than doubling the number of CPU cores in comparison to last year.
Thankfully, due to some nice contributors, we were able to run some
high-performance CPUs including a MPI cluster continuously throughout
the contest.
Software
| Crackers | Parsers
|
| InsidePro Extreme GPU Bruteforcer (EGB) | Unified List Manager (ULM)
|
| InsidePro PasswordsPro (Ppro) | EGB Utilities
|
| Hashcat-plus | Hashcat Utilities
|
| Hashcat |
|
| Hashcat-lite |
|
| John the ripper (JtR) |
|
| Passrecovery Suite |
|
| Passware Kit |
|
| Hashkill |
|
| Archive Password Recovery |
|
| Elcomsoft Forensic Disk Decryptor |
|
We were equipped with a plethora of password `cracking' software, which
enabled it to audit a multitude of algorithms ranging from simple md5
to md5(sun) and everything in between. In addition, custom modules were
coded where necessary for Ppro and EGB to support algorithms such as
`bwtdt' and mssql2012, unsuccessful attempts were also made to code
software for RC2. The `cracking' software was supported with a number
of list parsers and generators that enabled us to adapt to the
patterned passwords by generating targeted lists highly specific to the
group of hashes we were attacking.
The Game
Once the files were decrypted, our team spent the first 1.5-2 hours
identifying the different hashes by running sample cracks and linking
them to the correct algorithm. Grouping the hashes by algorithm
allowed the simpler algorithms such as MD5, NTLM to be attacked in
batch. The hashes were also indexed both by company and by algorithm.
TeamLogic, our HMS, was then recoded on-the-fly to distinguish between
the hashes from each company and also by algorithm. In addition,
implementation for the wide array of algorithms was gradually coded to
support the different hashes. While there was a short period of
down-time initially to get all the hashes sorted, it really paid off in
the long run.
Our usual free-for-all approach was taken in the early stages of the
contest, allowing us to gather as much plaintext data as possible which
could be applied to the `tough' algorithms. Broad sweeps were conducted
on the high-performance CPU processors for GPU unfriendly algorithms
early on, but didn't yield any positive results.
After one of our submissions, we noticed there was a `plaintext'
collision for SHA512(unix); where the same plaintext was used twice for
different algorithms. There was only one problem; it was 1 out of
17,000 plaintexts, so it was literally finding a needle in the
haystack. At this point we made the decision to dedicate some CPUs in
finding out what the plaintext was. After some time with 38 CPUs we
found the plaintext to be a hockey team suffixed with 1 number. Lists
were immediately generated for the hockey teams and tasks were
distributed to cover the dict + ?d, dict + ?d?d, dict + ?d?s, ?s + dict
masks for SHA512(unix) on GPU which led us to a comfortable start.
Roughly 5 hours into the competition we had identified breaks for
MD5(sun) involving the [-1 01 -2 012345] ?1?d:?2?d:?2?dAM and
?1?d:?2?d:?2?dPM exploits. Covering the mask at the rate of 11 words/s
required some more processing power. The hashes for the particular
company were isolated and distributed into chunks. In addition to
placing almost all the high-performance CPUs onto this algorithm
throughout the contest, another 28 hours worth of EC2 (cc2.8xlarge)
instances were initiated dedicated to this mask. Standard CPUs were
also used in attacking this mask and we had submissions for MD5(sun)
coming in till the final hours of the contest.
Almost 11 hours in, we had our first Blowfish break which yielded a hit
from small names list. Some CPU cores where then assigned to this list
with a larger names list. A few more hits were obtained and it was
deduced that the names were Arabic. Arabic name lists were then put
against the Blowfish hashes giving us surprisingly good results. The
same list was also tested against other algorithms from the same
company yielding good results for SHA512(unix) as well.
While an earlier version of the `passwordPASSWORD' was generated
containing names only, we later isolated another `passwordPASSWORD'
list which was more compact and optimized to give positive results
across a large number of algorithms including md5(unix), DRUPAL, and
des(unix). Some other patterns we identified included the use of plane
models for company 3, the use of scientific terms and bacteria names
with rule modifiers for company 5. Applying substitution rules `sa@ and
ss$' and ?d?d suffix modifiers on the Arabic names list mentioned
above, gave further hits for algorithms of company 3. We also saw the
return of the `elements' list used in conjunction with rule modifiers.
A special wines list was also crafted and attacked with using
1960?s-2013?s mask prefix for company 2. We also identified some animal
based passwords which would work well with some prefix/suffix
modifiers. Equation based passwords were also noticed, such as
`739%411=328' and a math oriented dictionary generator was explicitly
coded by `Matermind' to exploit this pattern across a series of
algorithms.
Towards the end, all effort was focused on a distributed SHA512(unix)
attack, using a specially designed list with the ?d prefix modifier,
which gave us substantial hits consistently until the final minute of
the contest.
Rather than bore you with every minute detail and going through all the
algorithms and hashes. Here are some visuals which we won't be
elaborating on, but should provide some insight into the plaintexts we
recovered.
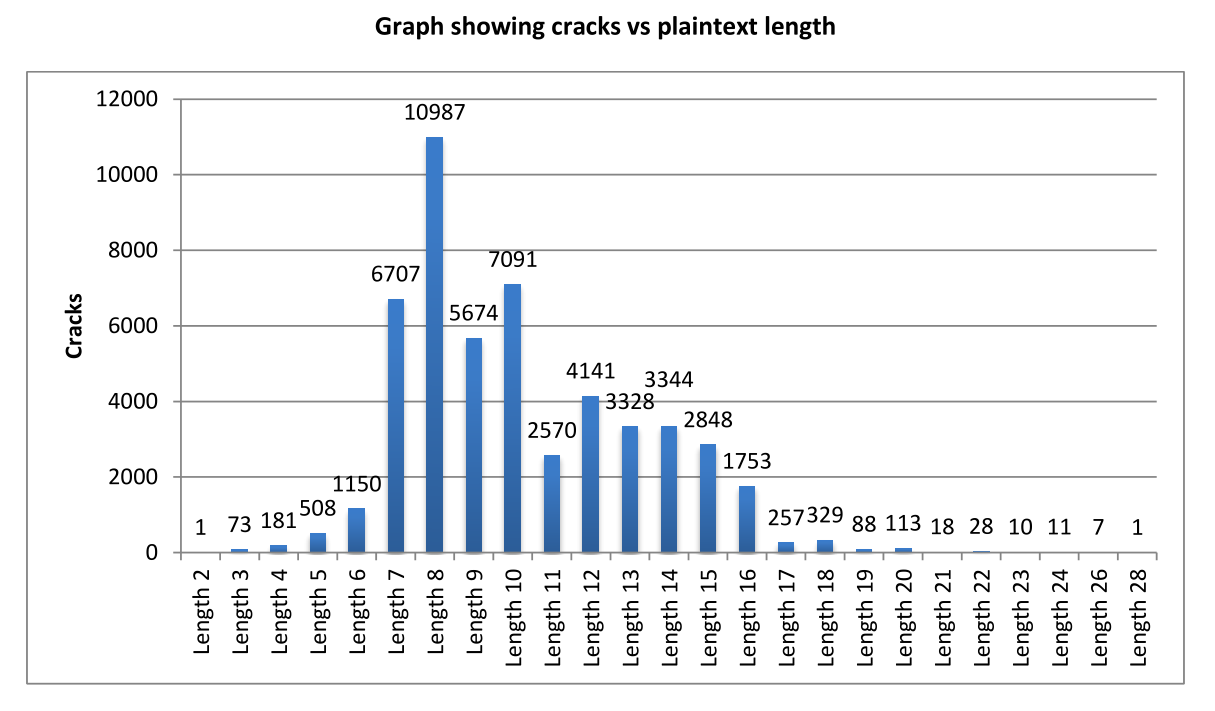
Average plaintext length: 10.2
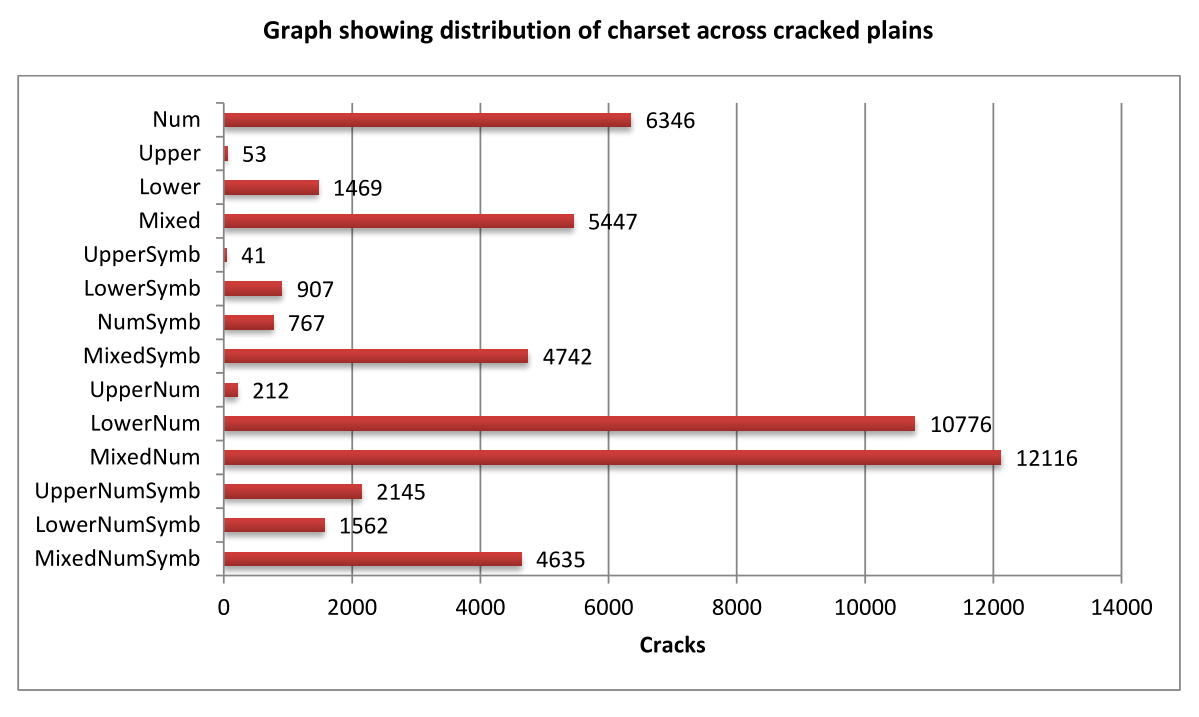
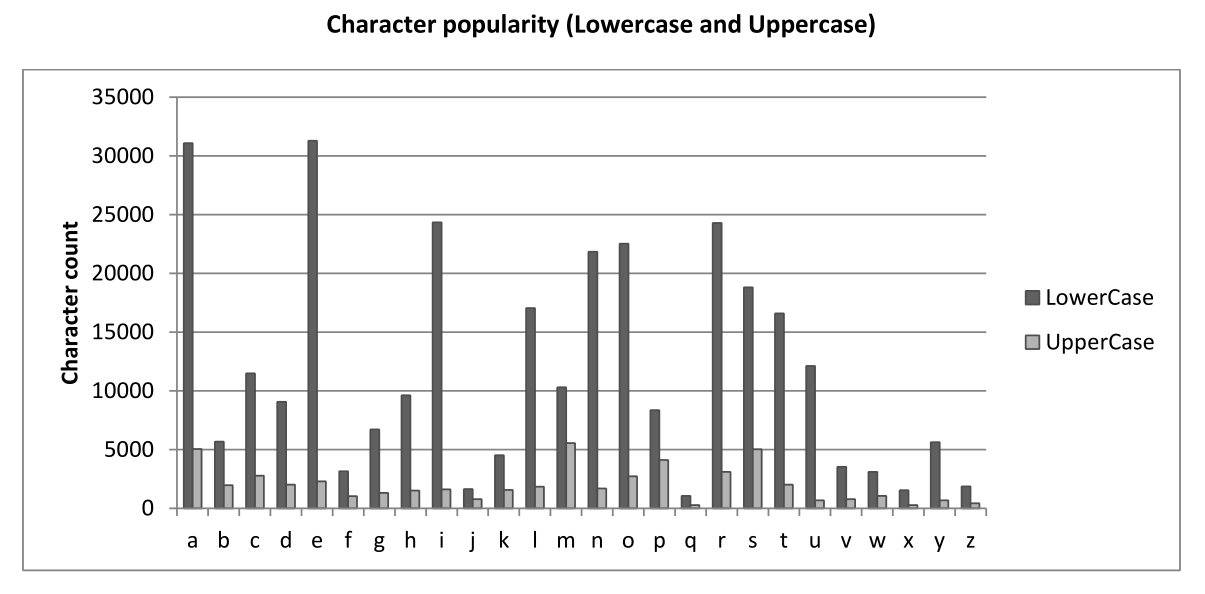
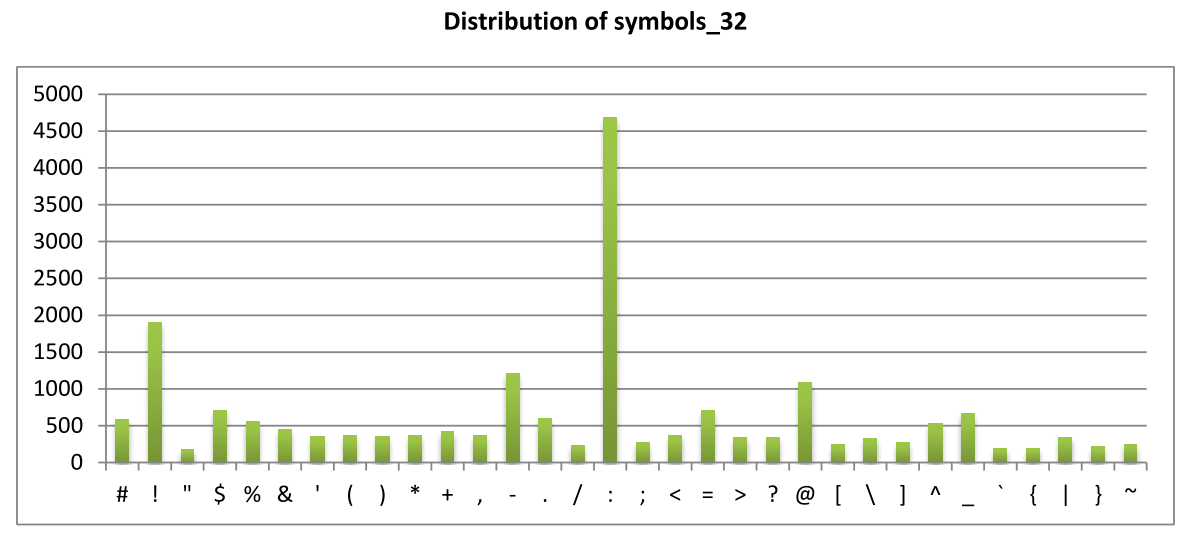
Challenges
Aside from the easy MD5 challenge which involved unmasking of hashes,
most of the other challenges appeared to be quite hard. We were able to
extract roughly 15,000 SSHA hashes from challenge 3. However, we
weren't able to crack a single one, we assumed either long/strange
passwords used or we had invalid hashes. We tinkered around with the
OSX plist files before realizing JtR from the bleeding-jumbo branch
came with scripts to convert them to useable hashes#.which we couldn't
load into JtR 1.7.9-jumbo7. The `easy' pdf and `7zip' files didn't seem
easy at all.
Coding
Some coding was carried out this year to take on some of the newer
algorithms in the form of add in modules for Ppro and EGB including
`bwtdt' and in addition having a GPU implementation of mssql2012 really
has its benefits. Unsuccessful attempts were also made at cracking the
mysterious RC2 hashes, which results in lots of peculiar but meaningful
collisions. It was also great to be able to preview some of InsidePro's
developmental projects.
Some remarks
We had really great team dynamics, cohesion and organization. We were
able to identify patterns very quickly enabling us to converge our
attacks towards particular lists and algorithms. We had more than
enough distributed tasks going at any one time, which prevented idling
cores. Although we had minor outages and hiccups along the way, we were
able to persevere on. Efficient teamwork and effective communication
played integral roles in this competition.
Taking a defensive strategy we held onto to the MD5(sun) high value
hashes as security. We did this as a countermeasure against the tactics
employed by the other teams in previous years, which would scoop us in
the final hours of the contest. While we waited in baited breath
anticipating either Team Hashcat or John-users to drop a load of
surprise hashes which they are renowned for, it unfortunately never
came. Instead we decided to take the lead submitting all the MD5(sun)
at once, which led to a humongous lead. While Hashcat and our team
coincidently traded places between submissions we had plenty of
patterns for the tough algorithms allowing us to ultimately win. It
appeared that john-users either couldn't identify the patterns for the
tougher algorithms, or were too strongly focused on the file challenges
or lower scoring hashes.
It was quite strange to see the OSX 10.8 hashes worth so few points
considering the complexity of the algorithm and the high iteration
count. These hashes probably should have been worth the most.
It was thoughtful of Korelogic to implement a second division for
smaller teams and competitors. We thought this was a great idea to
enable a broader range of players without having to impose any
compromises, restrictions or rules on the larger teams.
Final words
Although we placed first based on points, Team Hashcat showed their
dominance, beating us in `raw cracks', while John- users demonstrated
their expertise in cracking a diverse range of algorithms including a
very tough challenge 9. These teams are truly rivals not to be reckoned
with.
If you have further questions or queries do not hesitate to drop into
our forum @ http://forum.insidepro.com
That's it from us.
Team InsidePro signing out.




